Xmlrpc.php was a groundbreaking solution. It facilitated remote communication with your WordPress site. This means you could manage your site from afar, using various apps or services. Imagine posting a blog from a smartphone app or integrating your site with other web applications – that’s the magic xmlrpc.php brought to the table.
As with any open door in technology, it didn’t take long for unwelcome visitors to find it. The primary issues stem from security vulnerabilities and brute force attacks, exploiting this very accessibility to try and break into your site. Furthermore, excessive requests to xmlrpc.php can lead to resource depletion, slowing down your site or even causing downtime.
Symptoms of the issue
The troubles with xmlrpc.php aren’t one-size-fits-all. Depending on your hosting environment, WordPress configuration, and how attackers target your site, you might run into a variety of symptoms:
- Increased server resource usage leading to slow website performance.
- Security vulnerabilities exposed to brute force attacks.
- DDoS (Distributed Denial of Service) attacks, exploiting xmlrpc.php to overwhelm your site.
- Continuous POST requests to xmlrpc.php visible in your access logs.
- Each of these symptoms points back to the same root cause but manifests differently depending on the attacker’s methods and your site’s specific setup.
Understanding the vulnerabilities
The presence of xmlrpc.php in WordPress, despite its known vulnerabilities and the availability of better alternatives like the WordPress REST API, is a classic example of the platform’s commitment to backward compatibility. This commitment ensures that websites running on older versions of WordPress, which rely on XML-RPC for external communication, continue to function without disruption. Now, let’s delve into the specific vulnerabilities associated with xmlrpc.php and understand why it’s considered a security risk.
Brute force attacks
xmlrpc.php can be exploited for brute force attacks. Unlike traditional brute force attacks that attempt to log in via the wp-login.php file and can be easily detected and blocked, an attack through xmlrpc.php can use system.multicall to test hundreds of password combinations with a single request. This not only makes the attacks harder to detect but also more efficient for the attacker.
When xmlrpc.php processes a request, it requires authentication, which traditionally involves sending the username and password with each request. This method, while straightforward, is inherently insecure.
Exposure to Brute Force Attacks
Each request being accompanied by a username and password combination offers an opportunity for hackers to attempt a brute force attack. They can automate requests to xmlrpc.php, cycling through countless combinations of usernames and passwords in an attempt to find the right one. If they succeed, they gain unauthorized access to the site, potentially allowing them to insert malicious content, delete crucial code, or otherwise compromise the site’s integrity.
Repeated authentication attempts
Since xmlrpc.php authenticates every single request, it provides a vector for sustained attacks without the need for sophisticated techniques. This simplicity makes it an attractive target for attackers looking to gain entry into WordPress sites.
How the REST API enhances security
The WordPress REST API represents a significant step forward in terms of security, especially regarding authentication. Instead of relying on username and password combinations for every request, the REST API can use OAuth — a more secure standard for access delegation. OAuth works by issuing tokens to applications after the user approves access. These tokens are then used for authentication, rather than transmitting sensitive credentials. Even if an attacker were to intercept a token, these tokens are often short-lived and can be revoked, minimizing potential damage.
DDoS attacks
Distributed Denial of Service (DDoS) attacks can also be facilitated through xmlrpc.php. Attackers can use the pingback feature (intended for notifying other sites of links) to send a flood of requests to a target website, overwhelming it and potentially causing downtime.
How it works
The functionality of pingbacks and trackbacks, enabled by xmlrpc.php, once served as a cornerstone of the blogging community. It fostered an interconnected ecosystem where bloggers and content creators could acknowledge and link to each other’s work, creating a web of interactions. However, as we transition into a more modern web with the adoption of the WordPress REST API, the legacy features of XML-RPC, including pingbacks and trackbacks, have become less essential and, unfortunately, a potential vector for cyberattacks.
How pingbacks and trackbacks become a liability
The mechanism of abuse:
Pingbacks and trackbacks, by their nature, were designed to notify you when someone else linked to your content. This was achieved through an automated handshake facilitated by xmlrpc.php. While the intention behind this feature was to enhance connectivity and engagement across the WordPress ecosystem, it inadvertently opened a door for malicious actors to exploit.
A hacker can initiate a Distributed Denial of Service (DDoS) attack using this very mechanism. By leveraging xmlrpc.php, they can send a flood of pingback requests to your site from numerous sources. This isn’t just a trickle of notifications but a deluge, capable of overwhelming your server’s resources. The outcome? Your site slows down to a crawl or, in worse cases, becomes completely inaccessible, effectively putting you out of action.
The impact of such attacks
The ramifications of a successful DDoS attack on your site are multifaceted:
Downtime: The most immediate effect is downtime. Your site becomes unavailable to visitors, which can hurt your reputation, user experience, and potentially your revenue.
Resource drain: Your hosting resources are consumed by handling the influx of fake pingbacks, which might lead to additional hosting costs.
Search engine ranking: Extended downtime or slow site performance can negatively affect your site’s SEO, potentially lowering your ranking in search results.
Security compromise: While the attack itself might not steal data, the strain it puts on your site’s defenses could open the door to other vulnerabilities being exploited.
Amplification attacks
The pingback feature can also be abused in amplification attacks, where small requests sent to `xmlrpc.php` are used to generate larger responses from the server. This can magnify the amount of traffic directed at a target, exacerbating the impact of DDoS attacks.
Check if xmlrpc.php enabled on your site
Identifying whether xmlrpc.php is active and accepting requests on your WordPress site is an essential step in enhancing your site’s security. Since simply having the file in your WordPress installation doesn’t necessarily mean it’s enabled or accessible, using tools like the XML-RPC Validator Web App can provide clear insight. Let’s break down the steps for identifying the status of xmlrpc.php and how to disable it if it’s still active.
How to check if xmlrpc.php is enabled
Use the XML-RPC Validator Web App:
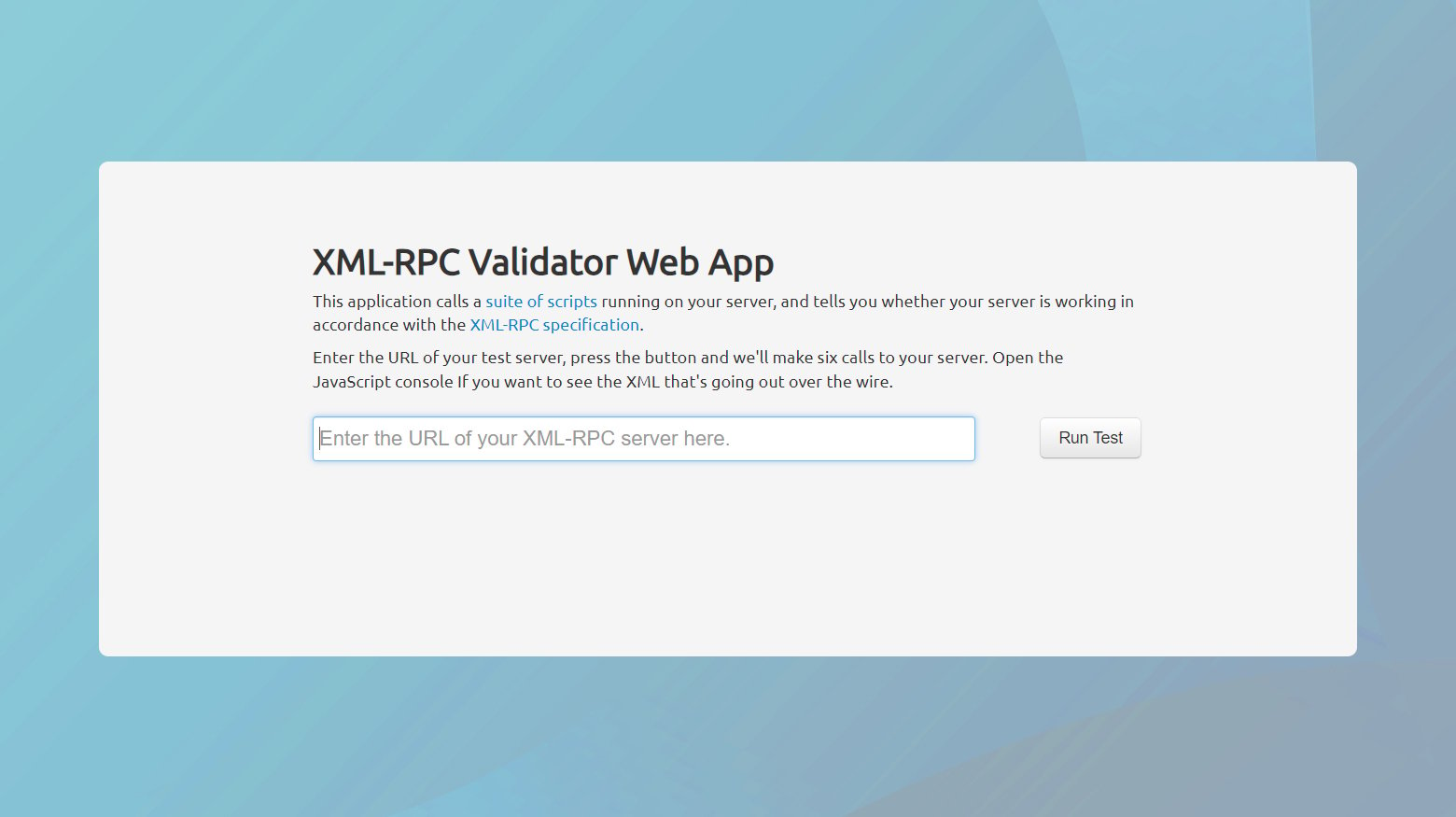
- Navigate to the XML-RPC Validator Web App.
- Enter your site’s URL.
- Run the test.
The validator will attempt to make a request to xmlrpc.php on your site and analyze the response.
If the test concludes that xmlrpc.php has been disabled, you’re in the clear. However, if the validator indicates that xmlrpc.php is active, you’ll want to take steps to disable it.
This tool is a straightforward way to test the XML-RPC functionality without having to dig into code or server settings yourself.
The case for disabling xmlrpc.php
While xmlrpc.php played a pivotal role in the past, the WordPress REST API has since taken the baton, offering a more secure, efficient, and flexible way for external applications to interact with WordPress. The REST API is like the upgraded version of xmlrpc.php – think of it as going from a flip phone to a smartphone.
Here’s why disabling xmlrpc.php is worth considering:
Security: xmlrpc.php is notorious for being a target for brute force attacks. Disabling it shuts down one pathway attackers can use to compromise your site.
Performance: Unnecessary xmlrpc.php calls can put a strain on your server resources. If you’re not using it, turning it off can lighten your server’s load.
Modern solutions: With the WordPress REST API, you have a modern, robust alternative that covers all the bases xmlrpc.php did but in a more secure and efficient manner.
Disabling xmlrpc.php
Disabling the xmlrpc.php file in WordPress is a crucial security step. Here, we’ll explore not just the plugin method but also a manual approach for users who prefer or need a more hands-on solution.
Using a plugin to disable xmlrpc.php
Installing a plugin, such as the Disable XML-RPC plugin, is the simplest and most straightforward method to disable xmlrpc.php. Plugins offer a user-friendly interface that requires minimal technical knowledge. They can effectively disable the XML-RPC functionality without altering any core WordPress files, thereby reducing the risk of breaking your site. This method is particularly advantageous for users who are not comfortable editing their website’s .htaccess file or those who do not have access to their site’s server files.
Step-by-step instructions
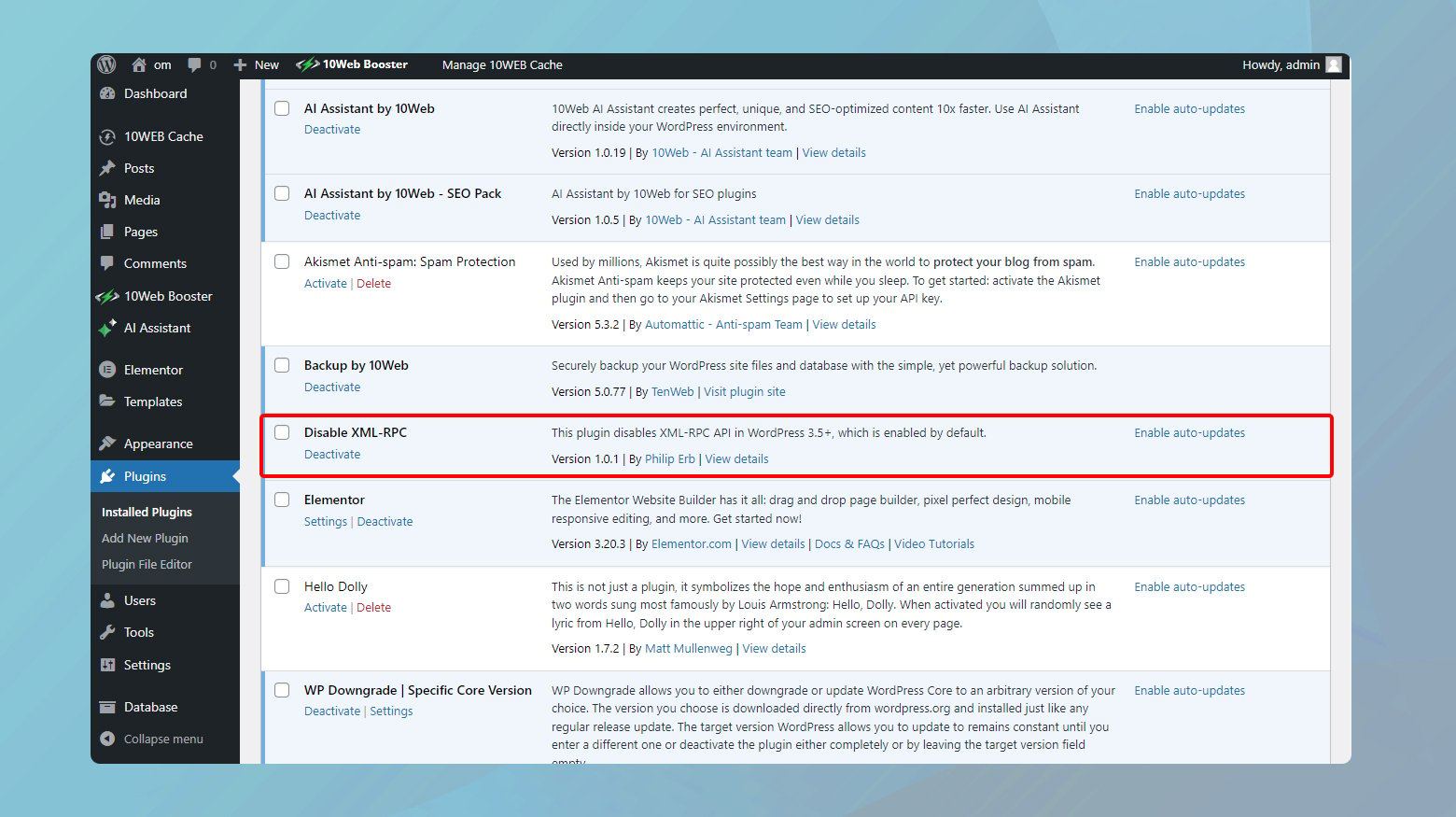
- Log into your WordPress dashboard.
- On the left sidebar of the dashboard, click on Plugins > Add New.
- In the search bar, type Disable XML-RPC and press Enter. This will bring up the plugin in the search results.
- Click on Install Now next to the Disable XML-RPC plugin. WordPress will download and install the plugin.
- After installation, click the Activate button. Activation is immediate, and no further setup is required.
Once activated, the plugin automatically disables xmlrpc.php, enhancing your site’s security with minimal effort.
Selectively disabling pingback functionality in xmlrpc.php
While completely disabling xmlrpc.php enhances WordPress security, it might limit functionality for some users who rely on remote publishing or other features that xmlrpc.php provides. For those who need to retain certain XML-RPC functionalities but want to disable the pingback feature—often exploited in DDoS attacks—the Disable XML-RPC Pingback plugin is an ideal solution.This approach provides a balanced solution that enhances security without sacrificing functionality.
Step-by-step instructions
- Start by logging into your WordPress site’s admin area.
- On the dashboard’s left-hand side menu, click Plugins > Add New to access the plugin repository.
- Search for Disable XML-RPC Pingback and hit Enter.
- Click Install Now > Activate to enable the plugin on your site.
Upon activation, the plugin immediately disables the pingback functionality of xmlrpc.php. There is no need for further configuration. Other XML-RPC features remain intact and operational, ensuring you can continue to enjoy the benefits of remote publishing and other XML-RPC-based functionalities without exposing your site to the security risks associated with pingbacks.
Fine-grained control with REST XML-RPC Data Checker
For WordPress site administrators seeking comprehensive control over both xmlrpc.php functionality and the REST API, the REST XML-RPC Data Checker plugin offers an advanced solution. This plugin not only allows for the fine-tuning of xmlrpc.php settings but also provides extensive control over the REST API, making it an indispensable tool for enhancing site security and functionality according to specific needs.
Step-by-step instructions
- Log in to your WordPress admin account.
- Click on Plugins > Add New.
- Search for REST XML-RPC Data Checker.
- Click the Install Now > Activate.
Configuring xmlrpc.php and REST API settings
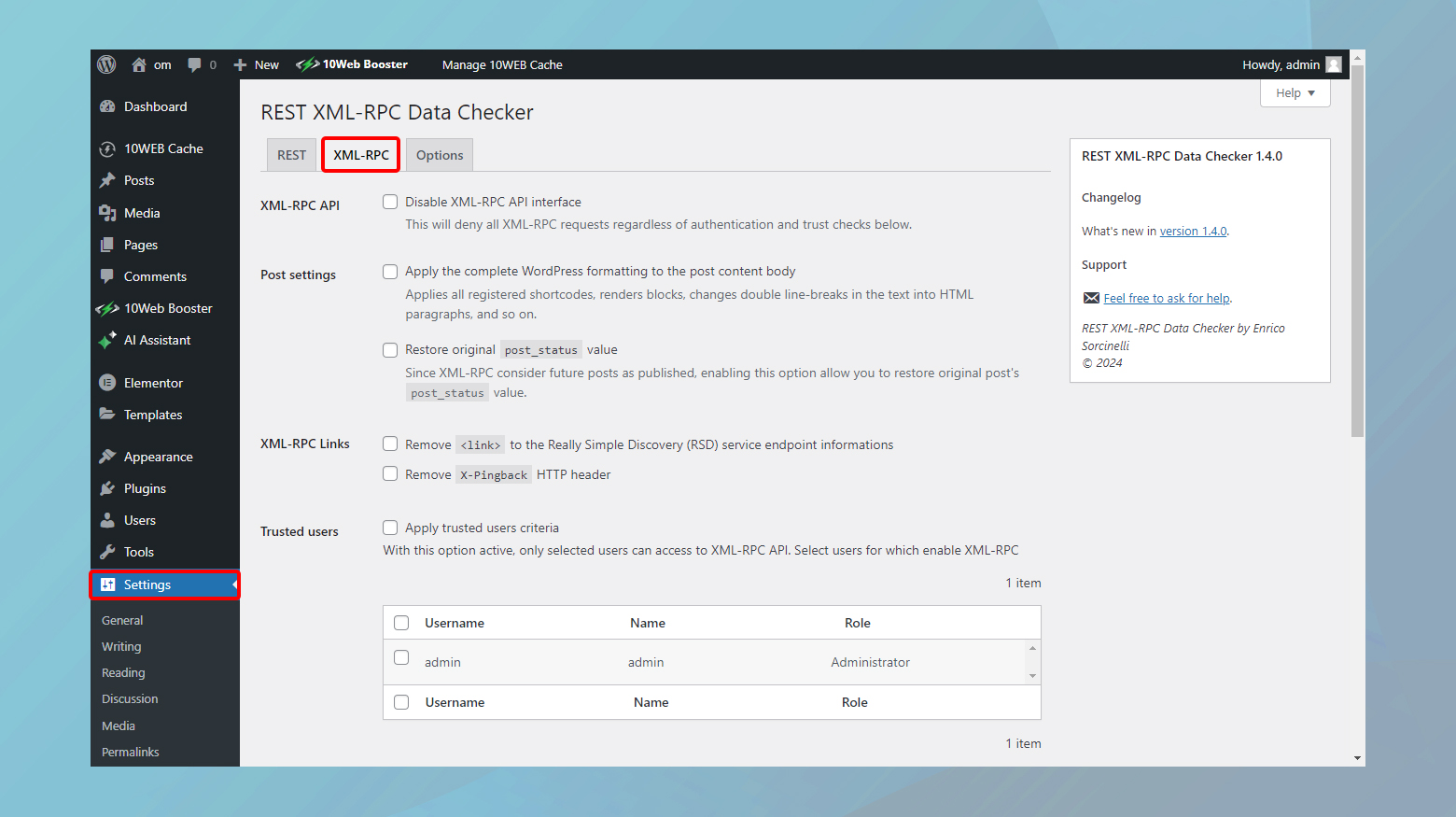
- From your WordPress dashboard, go to Settings > REST XML-RPC Data Checker. This will take you to the plugin’s configuration page.
- Click on the XML-RPC tab. Here, you’ll find options to enable or disable specific functionalities of xmlrpc.php. You can choose to disable the entire XML-RPC protocol or select certain aspects of it to remain active according to your needs.
- Switch to the REST API tab to configure settings for the REST API. Similar to the XML-RPC settings, you can enable or disable specific endpoints or functionalities, offering tailored control over how external applications interact with your site via the REST API.
Using the xmlrpc_enabled Filter to disable xmlrpc.php
Implementing the xmlrpc_enabled filter within a custom plugin is recommended over adding custom code to your theme’s functions file. This approach ensures that the changes remain in effect regardless of theme updates or changes, providing a more stable and reliable way to disable xmlrpc.php. Plugins offer a modular way to add or remove functionality without affecting the core system or theme files, making it a best practice for custom WordPress development.
Step-by-step Instructions
Using a text editor, create a new PHP file. You can name this file anything, but for clarity, something like disable-xmlrpc.php would be appropriate.
Paste the following code into your new file. This code snippet includes a standard plugin header followed by the filter that disables XML-RPC:
<?php
/**
* Plugin Name: Disable XML-RPC
* Description: Disables XML-RPC functionality on WordPress.
* Version: 1.0
* Author: Your Name
*/
add_filter( 'xmlrpc_enabled', '__return_false' );
- Connect to your WordPress site via FTP or your host’s file manager.
- Navigate to the /wp-content/plugins/ directory and upload your disable-xmlrpc.php file.
- Log into your WordPress dashboard, go to the Plugins section, and you’ll see your newly created plugin listed.
- Click Activate next to your plugin’s name.
Manually disabling xmlrpc.php via the .htaccess file
For users seeking more control or those who wish to minimize the number of plugins on their site, manually disabling xmlrpc.php is a viable option. This method involves editing the .htaccess file, which is a powerful configuration file used by Apache web servers. By adding a specific rule to this file, you can block access to the xmlrpc.php file, thus preventing potential attackers from exploiting it.
Before making any changes to the .htaccess file, it’s crucial to create a backup.This ensures that you can quickly revert to the original state if anything goes wrong.
Step-by-step instructions
-
- Connect to your website server via an FTP client or your web host’s file manager.
- Navigate to the root directory of your WordPress installation.
- Within the root directory, find the .htaccess file. This file may be hidden, so ensure your file manager is set to show hidden files.
- Right-click on the .htaccess file and select the edit option. If using an FTP client, you may need to download the file to edit it locally and then re-upload it after making your changes.
- At the end of the file, add the following lines to disable xmlrpc.php:
<Files "xmlrpc.php"> Require all denied </Files>
- Save your changes and, if editing locally, upload the modified .htaccess file back to the root directory of your WordPress site.
This manual approach effectively blocks access to the xmlrpc.php file, thereby securing your WordPress site from related vulnerabilities.
Talk to your hosting provider
Certain hosting services, recognizing the security vulnerabilities associated with xmlrpc.php, may automatically disable access to this file under threat conditions. This automatic intervention is designed to protect websites hosted on their servers from becoming victims of brute force or DDoS attacks facilitated through xmlrpc.php.
When a hosting provider disables xmlrpc.php, any request to this file will result in a 403 Forbidden error. This response is a server’s way of telling a client that it understood the request but refuses to authorize it. In the context of security, it’s an effective method to halt ongoing attacks by denying access to the targeted resource.
Before implementing any changes to disable xmlrpc.php, it’s wise to consult with your hosting provider. They may already have security measures in place or offer recommendations tailored to their hosting environment. Moreover, understanding your hosting provider’s policies and capabilities can guide you in choosing the most effective and compatible method for securing your site.
When to enable xmlrpc.php on your WordPress site
While the general advice for modern WordPress sites is to disable xmlrpc.php due to security concerns, there are specific scenarios where enabling it may be necessary or the only option available.
Lack of REST API usage
Your WordPress site does not utilize the REST API, but there’s a need to communicate with other systems or applications. This might be due to the specific requirements of those systems or applications that are only compatible with XML-RPC.
In such cases, xmlrpc.php acts as a bridge for remote communication, enabling functionalities like remote posting or integration with external content management tools.
Inability to update WordPress
You are running a WordPress version older than 4.4, which does not include the REST API feature. This could be due to restrictions imposed by your hosting environment or incompatibilities with your current theme or plugins.
If updating WordPress is not feasible due to these limitations, xmlrpc.php remains a critical component for remote interactions. However, it’s advisable to address the root cause—be it changing the hosting provider or updating incompatible themes or plugins—to secure and modernize your site.
External application compatibility
Your site needs to work with an external application that lacks support for the WP REST API but is compatible with XML-RPC. This situation is increasingly rare but may occur in legacy systems or specialized software.
While temporarily relying on xmlrpc.php for such integrations, planning for the long-term migration to REST API-compatible applications is crucial. This ensures future-proofing your site and maintaining compatibility with the latest web standards and security practices.
Tips
- Transitioning to the REST API for remote communications and integrations offers more flexibility, security, and compatibility with contemporary web ecosystems.
- Prioritize keeping WordPress and all associated themes and plugins up to date. This not only ensures access to the latest features and security improvements but also reduces the need for legacy solutions like XML-RPC.
- If you’re in a situation that necessitates the use of xmlrpc.php, consulting with web development and security professionals can provide alternatives or mitigate potential risks.
Closing thoughts
In our blog, we’ve looked at what xmlrpc.php is and how it is used both by website owners and hackers. We have also covered the significance of disabling xmlrpc.php in WordPress for security reasons, while also recognizing exceptions where its use might be necessary. We delved into methods for deactivation via plugins, custom code, and .htaccess modifications, emphasizing the role of hosting providers. Furthermore, we acknowledged scenarios requiring xmlrpc.php due to legacy systems or the absence of REST API support. The overarching advice leans towards disabling xmlrpc.php to bolster security, advocating for updates and the adoption of modern integration methods through the REST API. Create a custom WordPress website tailored to your business needs 10X faster with 10Web AI Website Builder.
Accelerate your WordPress website creation with AI
No credit card required