A website being hacked is a major concern for every site owner. Despite WordPress being a robust platform, no site is completely immune to security threats, particularly if appropriate safeguards haven’t been put in place.
However, if your WordPress site has fallen victim to a hack and the damage has been inflicted, don’t worry. There are several strategies you can use to retrieve lost content, mend the damage, and protect your site against potential future breaches.
How to know if your site has been hacked
When your website isn’t functioning as it should, there are some specifics you can look for in order to determine if this behavior is due to a hack.
Inability to log in: If you find yourself unable to log into your WordPress dashboard, it could be a sign that hackers have taken over your admin account. They might have changed your password, or worse, deleted your account entirely. This is often one of the first alarming signs that unauthorized changes are happening on your site.
Unexpected site changes: Noticing changes on your site that you didn’t make is a clear red flag. This could manifest as a new homepage, added content, or even new plugins or themes that have been installed without your knowledge. Hackers might use your site to distribute malware, create phishing pages, or simply vandalize your website to demonstrate their ability to breach your security.
Site redirects: When your site redirects visitors to unfamiliar sites, especially those laden with ads, malicious content, or phishing schemes, it’s a telltale sign of a hack. Hackers can insert redirection code into your site files or database, exploiting vulnerabilities to reroute your traffic for their gain.
Browser warnings: If you or your users encounter a browser warning when trying to access your site, indicating it’s unsafe or has been compromised, it’s a serious indicator of a security breach. Search engines and browsers have mechanisms to detect and warn users about sites containing malware or exhibiting suspicious behavior.
Search engine warnings: Similar to browser warnings, if Google or any other search engine flags your site with a warning like “This site may be hacked,” it means they’ve detected malware or spam content. Search engines constantly scan websites for malicious activities to protect users, and being flagged can significantly impact your site’s traffic and trustworthiness.
Security plugin notifications: If you have security plugins installed, receiving notifications about a breach, unusual activity, or unexpected changes to your site’s files is a clear indication of a hack. These plugins monitor your site for exactly this type of activity and can often provide early warnings before the effects are visible to users or administrators.
Hosting provider alerts: Hosting providers monitor their servers for unusual activity, such as spikes in traffic, bandwidth usage, or the presence of malware. If your hosting provider contacts you with concerns about your account, it’s a strong indication that your site has been compromised or is being used for malicious activities.
Understanding the implications
Each of these signs points to different methods of attack or areas of vulnerability within your WordPress site. From direct unauthorized access and modification of site content to more covert methods like inserting redirection scripts or malware, the range of hacking techniques is vast. Identifying the specific symptoms allows you to tailor your response and recovery efforts more effectively, ensuring you address the root cause of the breach.
Inability to log in
The inability to log into your WordPress dashboard is indeed a concerning symptom that could point to a security breach. Let’s look at this issue further, focusing on distinguishing between simple forgetfulness and signs of a hack, and what steps you should take in each scenario.
It’s not uncommon to forget passwords, especially if you manage multiple accounts or if it’s been a while since you last logged in. WordPress has built-in features to handle this, allowing you to reset your password via your email address.
Signs of hacking
If the password reset process doesn’t work, for example, if you don’t receive the password reset email (and it’s not in your spam folder), or if the reset link leads to an error page, these could be signs of interference by a hacker.
If you’re able to reach someone else with administrative access and they find that your user account is missing, altered, or has different permissions, this strongly indicates unauthorized access.
Unexpected site changes
The alteration of your WordPress site’s homepage or the injection of offensive content and links are common tactics used by hackers to either spread malware, promote other websites, or simply to vandalize. Here’s a closer look at this issue and how to approach it.
Signs of hacking
- Your site displays a static page you didn’t create, often with malicious or promotional content.
- Addition of content or external links that promote other sites, especially if these links are to offensive or illegal content. The inclusion of such links, especially when hidden or in tiny fonts, is a tactic to manipulate search engine rankings or direct your visitors to malicious sites.
- Your active theme may be switched without your knowledge, or you might notice alterations in its appearance or functionality that you didn’t authorize.
Before jumping to conclusions, verify with any co-administrators, editors, or contributors that they haven’t made the changes. Sometimes, well-intentioned updates or tests can go wrong.
If you’ve recently updated your theme, especially if it’s not from a reputable source, the update might have introduced malicious code or unwanted changes. Always use themes from trustworthy developers or the official WordPress theme repository.
Site redirects
Site redirection hacks can be particularly disruptive and damaging, not just to your site’s reputation but also to the user experience and trust of your visitors. These types of attacks exploit vulnerabilities to insert redirection code into your site’s files or database, causing visitors to be sent to unintended, often malicious sites. Let’s break down how these attacks happen, their implications, and the steps to resolve and prevent them.
How site redirection hacks occur
- Outdated themes or plugins can contain security vulnerabilities that hackers exploit to inject redirection scripts.
- Compromised admin accounts due to weak passwords can give attackers direct access to modify your site’s content or settings to redirect users.
- Vulnerabilities at the hosting server level can allow attackers to alter website files or databases across multiple sites hosted on the same server.
Browser warnings and search engine notifications
Browser warnings and search engine notifications are critical alerts that should never be ignored, as they often indicate a security breach that could have far-reaching consequences for your WordPress site. These mechanisms are in place to protect users from harmful content, and when they’re triggered for your site, it’s a clear signal to take immediate action.
Understanding browser warnings and search engine notifications
Browser warnings: Web browsers like Chrome, Firefox, and Safari use various security services to check websites for malicious activity. If they detect malware, phishing attempts, or other suspicious activities, they’ll display a warning to users attempting to access the site, often stating that the site is unsafe or has been compromised.
Search engine warnings: Search engines like Google monitor the websites they index for security issues. If they find malware or signs of a hack, they may display a warning in the search results, such as This site may harm your computer or This site may be hacked. Google Webmaster Tools (now Google Search Console) can provide site owners with alerts and details about these security issues.
Possible causes
Malware infection: Your site may be infected with malware designed to steal information, disrupt operations, or infect visitors.
SEO spam: Unauthorized content added to your site to boost other sites’ SEO can lead to warnings if detected by browsers or search engines.
Hacked sitemap: A compromised sitemap can mislead search engines about the content of your site, potentially leading to warnings and penalties.
Security plugin notifications
Security plugins play a crucial role in the early detection and mitigation of hacks on WordPress sites. By monitoring your site for suspicious activities, these plugins can alert you to potential security breaches before they escalate into more serious issues. Here’s how you can interpret and act on these notifications:
Understanding security plugin notifications
Breach notifications: Indicate that an unauthorized access or data leak has occurred. This could involve sensitive information being exposed or stolen.
Unusual activity alerts: Might include unexpected changes in traffic patterns, the creation of unauthorized user accounts, or modifications to files and content that were not initiated by you or other legitimate users.
File change warnings: Alert you to unauthorized modifications to your site’s core files, plugins, or themes. This can be a sign of malicious code being injected into your site.
Hosting provider alerts
When your hosting provider alerts you to unusual activity or concerns regarding your account, it’s a significant warning sign that should prompt immediate action. Hosting providers have a broad perspective on the traffic and behavior of the websites they host, and they can detect anomalies that may not be apparent to individual site owners. Here’s what such alerts might entail and how you can respond effectively.
Types of alerts from hosting providers
Spikes in traffic: An unusual increase in traffic could indicate a DDoS (Distributed Denial of Service) attack, where your site is being overwhelmed with requests to make it unavailable to legitimate users.
Bandwidth usage: Excessive bandwidth usage might be a sign that your site is serving large files (like videos or downloads) unknowingly, possibly due to malware distribution.
Presence of malware: Hosting providers may run their own scans for malware and can alert you if they find malicious software hosted on your site.
Blacklisted site: If your website has been blacklisted by search engines or internet security providers, your host may notify you since this can also affect the server’s reputation.
Common reasons leading to WordPress site hacks
WordPress, while being one of the most popular and user-friendly content management systems available, is not immune to security vulnerabilities. The reasons for WordPress sites getting hacked can often be traced back to a few common factors. Understanding these factors is key to protecting your site from unwanted intrusions.
Insecure passwords
Insecure passwords stand as one of the primary vulnerabilities exploited by hackers, particularly in WordPress sites. The simplicity and predictability of passwords such as password, 123456, or admin significantly lower the bar for unauthorized access, making brute force attacks not only possible but often successful. Here’s why strong passwords are crucial and how to implement them effectively:
The risk of insecure passwords
Brute force attacks: These attacks use automated software to generate and test thousands of password combinations in a short period. Simple and common passwords can be cracked in seconds.
Dictionary attacks: Similar to brute force, but using dictionaries of common passwords and phrases, making simple passwords particularly vulnerable.
Account takeovers: Once a password is compromised, attackers can gain full access to your WordPress site, potentially leading to data theft, site defacement, or the insertion of malicious content.
Characteristics of strong passwords
A strong password is your first defense against unauthorized access. Effective passwords should:
- Be at least 12 characters long, incorporating a mix of letters (both uppercase and lowercase), numbers, and special characters.
- Avoid predictable patterns and common phrases that can be easily guessed or found in a dictionary attack.
- Be unique, not reused across different sites or services to prevent a breach on one site from compromising another.
Outdated core, themes, and plugins
WordPress regularly releases updates that patch security vulnerabilities. Outdated WordPress core, themes, and plugins represent a significant security vulnerability, often serving as the easiest entry points for hackers. WordPress, being an open-source platform, regularly updates its software to patch security flaws, improve functionality, and add new features. When these updates are ignored, it leaves the door wide open for attackers to exploit known vulnerabilities.
Why updates are crucial
Security patching: Many updates address specific security vulnerabilities that have been discovered since the last version. By not updating, you’re effectively ignoring a fix for a known issue.
Bug fixes: Updates not only address security concerns but also fix bugs that could affect your site’s performance or functionality.
Feature improvements: Staying updated means you can take advantage of the latest features and improvements, which can enhance your website’s efficiency and user experience.
Risks of ignoring updates
- Hackers use automated tools to scan websites for known vulnerabilities. Outdated sites are easily identifiable and become prime targets.
- Successful exploits can lead to stolen data, including sensitive user information, which can have legal and reputational repercussions.
- Attacks might result in your site being defaced, taken offline, or used to distribute malicious software, impacting your credibility and SEO.
Nulled themes and plugins
Nulled themes and plugins represent a considerable risk to WordPress site security and integrity. These are pirated versions of premium themes and plugins that are distributed illegally on the internet, often free of charge. While the initial appeal of accessing premium features without cost is understandable, the use of nulled software carries significant risks that far outweigh any perceived benefits.
The risks of using nulled themes and plugins
Malicious code: One of the primary dangers of nulled themes and plugins is the potential inclusion of malicious code. This can range from backdoors that allow hackers to access your site undetected to malicious scripts that can steal user data or distribute malware to your visitors.
No updates or support: Legitimate premium themes and plugins come with the advantage of regular updates and developer support. Nulled versions, however, are cut off from these updates, leaving your site vulnerable to security exploits and compatibility issues.
Legal and ethical considerations: Using pirated software is illegal and unethical. It violates copyright laws and harms the WordPress community by depriving developers of the revenue needed to support and improve their products.
SEO penalties: Malicious activities conducted through nulled software can lead to your site being blacklisted by search engines, severely damaging your site’s visibility and reputation.
Security vulnerabilities: Nulled themes and plugins often go unnoticed in regular security scans because the malicious code within them can be deeply hidden, making it difficult to detect and remove.
Reputable sources
Not all plugins and themes are created equal. Installing extensions from unofficial or untrusted sources increases the risk of introducing vulnerabilities to your site. Selecting themes and plugins from reputable sources is a critical step in securing and ensuring the reliability of your WordPress site. The vast ecosystem of WordPress extensions offers immense functionality, but it also poses risks when not navigated wisely. Here’s why choosing reputable sources matters and how to do it effectively.
Why choose reputable sources
Security: Reputable sources conduct thorough reviews and regular updates to ensure themes and plugins are secure against known vulnerabilities.
Support: Premium themes and plugins from reputable providers come with professional support, helping you solve any issues that might arise.
Compatibility: Trusted developers ensure their products are compatible with the latest version of WordPress and with other popular plugins and themes, reducing the risk of conflicts.
Quality: Themes and plugins from reputable sources are more likely to follow WordPress coding standards, ensuring better performance and security.
Updates: Regular updates from trusted developers mean that any security vulnerabilities are promptly addressed, and new features are added to keep your site up-to-date.
Main routes used to hack WordPress sites
Backdoors: These allow hackers to bypass normal authentication methods, gaining unauthorized access to the site, often through scripts or hidden files. An infamous example is the TimThumb vulnerability.
Pharma hacks: This type of exploit is used to inject malicious code into outdated versions of WordPress, often to distribute spam or pharmaceutical ads without the site owner’s knowledge.
Brute-force login attempts: Hackers use automated tools to guess passwords and gain access to sites, exploiting weak passwords.
Malicious redirects: Through backdoors, hackers can insert code that redirects visitors to malicious sites, often for phishing or malware distribution.
Cross-site scripting (XSS): This vulnerability, often found in plugins, allows hackers to inject malicious scripts into web pages, which are then executed in the visitor’s browser.
Denial of service (DoS): Exploiting bugs or errors in website code, attackers can overwhelm a site with traffic, rendering it inaccessible.
What to do if your WordPress site has been hacked
If your WordPress site has been hacked, taking immediate and comprehensive action is crucial to regaining control, cleaning your site, and preventing future breaches. The steps required can vary based on the nature and severity of the hack, but a structured approach can help you navigate through the recovery process effectively.
Identify the hack
Identifying the extent and nature of a hack is the first critical step towards recovery for your WordPress site. Knowing what you’re dealing with can help you choose the most effective strategy for cleanup and future protection. Here’s how you can start the identification process:
Visual inspection: Check your site from the front end for any obvious signs of defacement. This could include unauthorized posts, comments, or changes in the site’s appearance.
Content and redirects: Look for any content that you did not create, such as spammy posts or pages. Check if your site redirects to other websites, particularly those that host malicious content or phishing schemes.
Access and permissions: Review the list of users in your WordPress dashboard. Be on the lookout for accounts you did not create, especially those with administrative privileges.
Check site performance: A sudden slowdown in site performance or an unexpected increase in bandwidth usage can also be indicators of a hack, as some attacks utilize your server resources.
Enable maintenance mode
Putting your WordPress site into maintenance mode is a smart move during recovery from a hack. It not only shields your visitors from potentially harmful content but also maintains your site’s professional appearance while you’re working on fixes. Here’s how to manage this process, whether or not you currently have access to your admin dashboard.
If you can access your WordPress dashboard
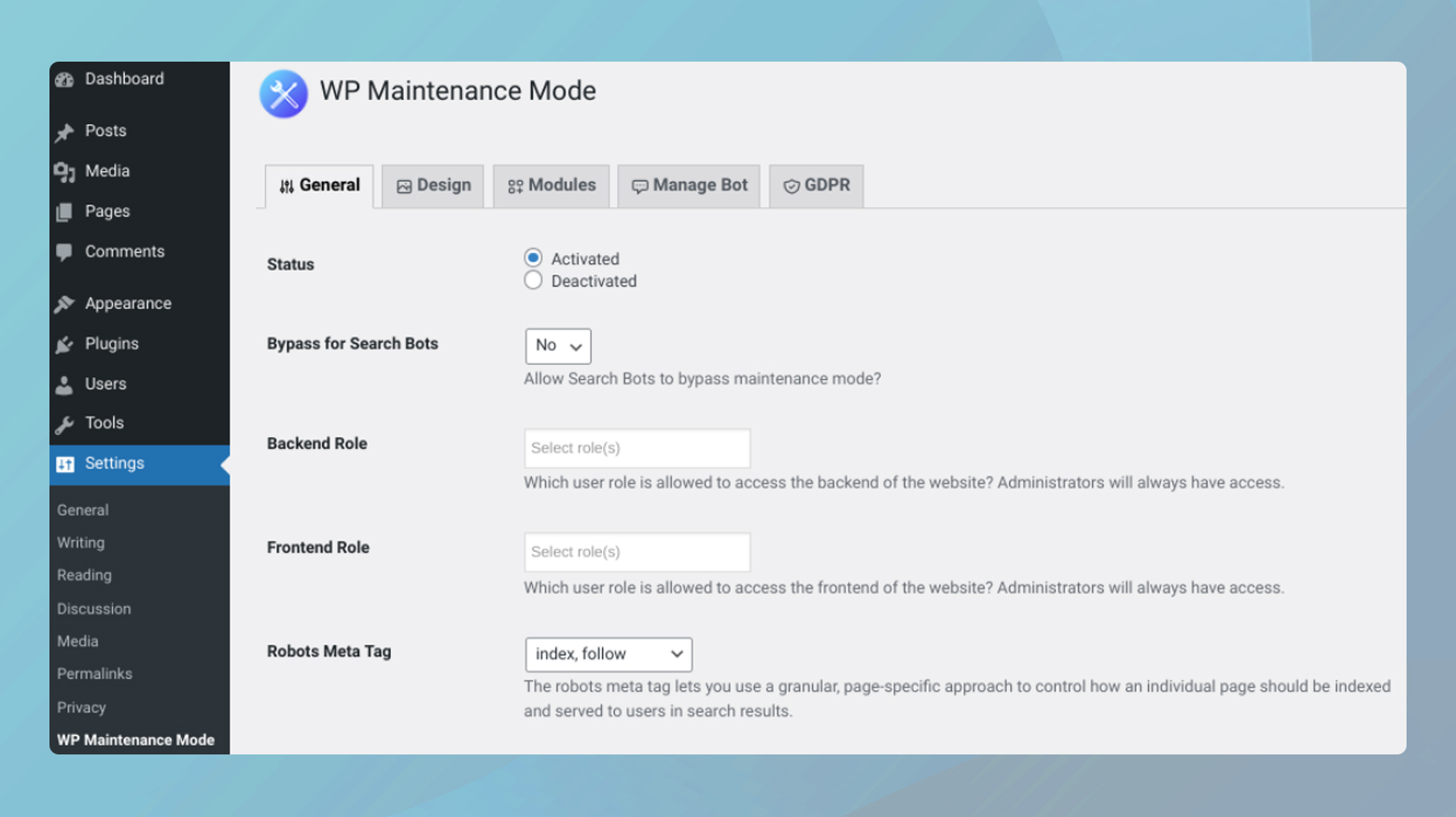
Plugins like Coming Soon Page & Maintenance Mode by SeedProd or WP Maintenance Mode are excellent choices. They allow you to activate maintenance mode and set up a custom message or page that visitors will see, explaining that your site is undergoing maintenance.
- Go to Plugins > Add New and search for the maintenance mode plugin of your choice.
- Click on Install and Activate it.
- After activation, locate the plugin settings in your WordPress dashboard.
- Customize the maintenance mode page to your liking and activate it.
Most plugins offer options for design, messaging, and even a countdown timer or a subscribe form.
If you cannot access your WordPress dashboard
If you’re locked out of your admin area, there are alternative methods to enable maintenance mode:
Via FTP
- Use an HTML editor to create a simple maintenance.html page. You can include a message informing visitors that the site is under maintenance.
- Connect to your site via FTP.
- Upload the maintenance.html file to your website’s root directory.
10Web’s malware removal program
If your website is hosted on 10Web, you can take advantage of 10Web’s malware removal program. 10Web’s comprehensive approach to WordPress site security showcases a strong commitment to maintaining the integrity and safety of the websites they host. For site owners, this service provides peace of mind and a practical solution to the ever-present threat of malware. Here are the key actions taken by the 10Web security team:
- Backup the website.
- Reinstall the WordPress core files.
- Change all SFTP, SSH, and database passwords.
- Remove any infected plugins or themes.
- Scan your website with 3rd party security software.
- Deactivate plugins temporarily.
- Remove Javascript injections from Pages or Posts.
- Enable maintenance mode.
10Web will take further steps if your website is in need of the removal of more complex malware and issues.
Change all passwords
After a security breach, resetting passwords across all access points is a foundational step in regaining control and securing your WordPress site from further unauthorized access. This comprehensive reset includes not just your WordPress admin password but also those used for SFTP, your database, and your hosting account. Here’s a more detailed look at why this is crucial and how to effectively manage this process.
Why change all passwords
It’s often unclear which password was compromised, making it essential to reset all to eliminate any backdoors the hacker might use for future access. Even after cleaning up malware or restoring your site, unchanged passwords remain a vulnerability for reentry. Hackers may create additional user accounts for persistent access. Resetting passwords and auditing user accounts can help prevent this.
Encourage all users, especially administrators, to reset their passwords. WordPress’s suggested password feature generates strong, complex passwords.
Navigate to Users > Your Profile in the WordPress dashboard to access this feature.
SFTP and hosting account passwords
Change these through your hosting provider’s control panel. Each provider has its own process, so consult their documentation or support if needed.
If you’re a 10Web user, you can generate a new SFTP password from your 10Web dashboard. Also, take a look at how to change your 10Web account password.
Database password
This can be updated through your hosting control panel, but remember to update your wp-config.php file with the new database password to maintain site functionality.
Updating WordPress core, themes, and plugins
Updating your WordPress core, themes, and plugins is a vital step in securing your site, especially after a hack. This process ensures that any known vulnerabilities are patched, reducing the risk of further attacks.
Before initiating any updates, it’s crucial to have a full backup of your WordPress site. This includes your website’s database, WordPress files, themes, and plugins. A backup allows you to restore your site to its current state if the update process causes any issues.
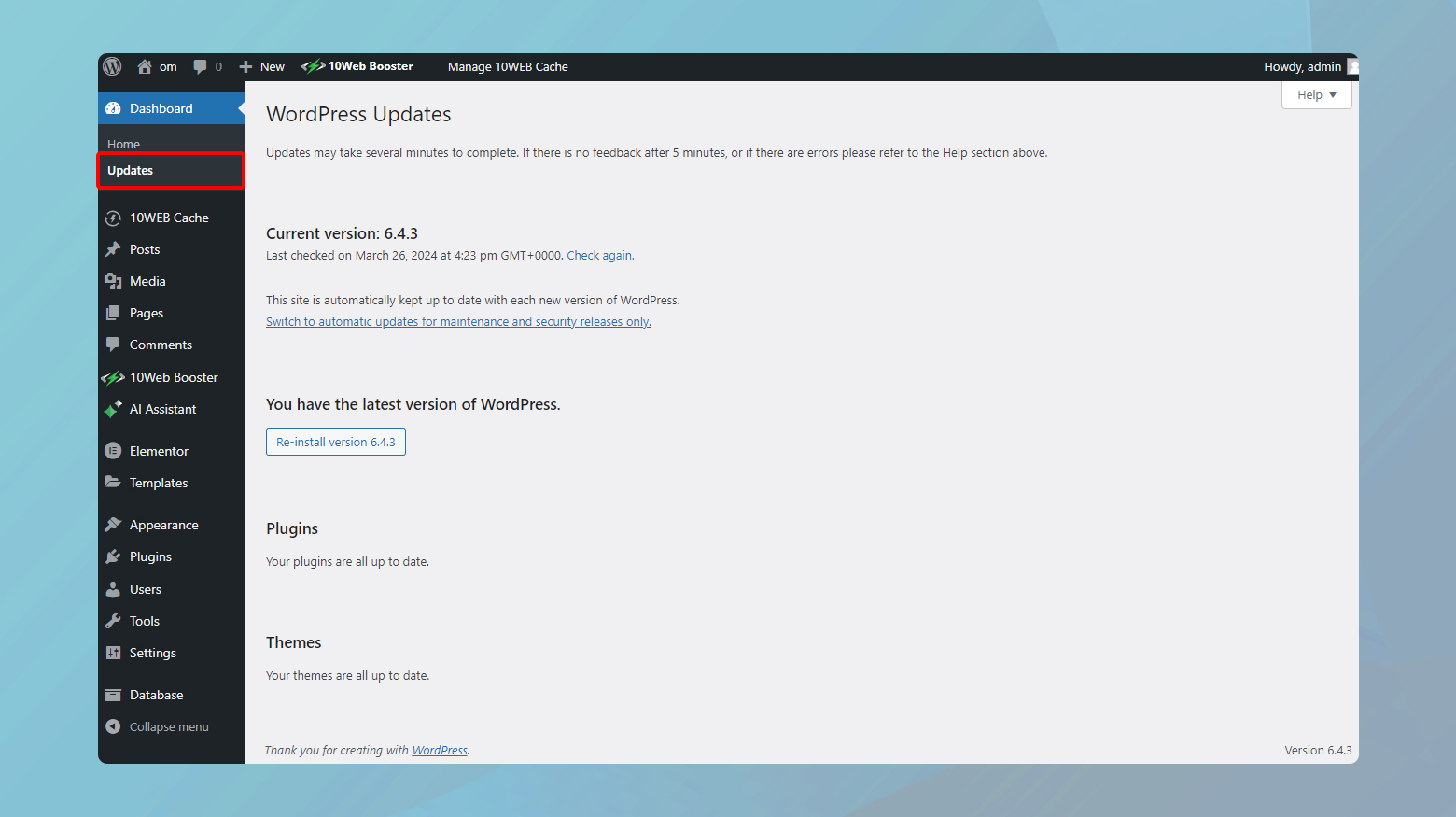
Update WordPress core

Updating the WordPress core should be your first step because many plugin and theme updates are designed to be compatible with the latest version of WordPress.
- Navigate to Dashboard > Updates in your WordPress admin area.
- If a new version of WordPress is available, you’ll see a message prompting you to update. Click the button to start the update process.
Update plugins and themes
After updating WordPress core, move on to your plugins and themes. This helps ensure compatibility and functionality across your site.
- Go to Dashboard > Updates. You’ll see a list of plugins that have updates available. You can select all plugins and update them simultaneously or update them one by one.
- In the same updates section, check for any available theme updates. Similar to plugins, you can update themes individually or all at once, depending on what’s needed for your site.
If your site uses WooCommerce, pay special attention to the order of updates to prevent potential conflicts that could affect your online store’s functionality.
- Update any WooCommerce extensions first. These are often tightly integrated with WooCommerce functionality and need to be compatible with the latest version.
- After updating the extensions, proceed to update the WooCommerce plugin itself. This ensures that your store remains functional and secure.
Delete users
Removing unauthorized admin accounts is a critical step in securing your WordPress site after a hack. Unauthorized access to your site’s admin area can lead to further security breaches, data theft, and site vandalism.
Before proceeding with the deletion of any admin accounts, it’s crucial to ensure that you’re not removing legitimate users who might have changed their details or whose accounts you might not immediately recognize.
- Reach out to all individuals who have or should have admin access to confirm their account details. This step helps prevent accidentally deleting legitimate accounts.
- If possible, review the activity logs for suspicious actions taken by admin accounts. This might include the creation of new users, unexpected changes to the site, or the installation of unfamiliar plugins or themes.
Remove unauthorized admin accounts
Once you’ve confirmed which accounts are unauthorized, you can proceed to remove them:
- In your WordPress dashboard, go to Users > All Users.
- Click on the Administrator link at the top to filter the list by users with administrator privileges.
- Check the box next to any user account that you have verified as unauthorized or suspicious.
- From the Bulk Actions dropdown menu, select Delete.
- Then click Apply. WordPress will ask you what to do with content owned by these users. You can choose to delete all content associated with them or assign it to another user.
Follow the prompts to confirm the deletion of the accounts. WordPress will remove the selected users and their associated content, based on your choices.
Important considerations
- Before deleting an account, consider the content (posts, pages, etc.) created by that user. WordPress will offer options to either delete their content or assign it to another user. Make a careful decision based on the content’s relevance and integrity.
- For remaining admin accounts, enforce a password change to ensure that all accounts are secure. Encourage the use of strong, unique passwords.
- Evaluate the necessity of each admin role. Limiting the number of users with administrative access can reduce your site’s vulnerability. Consider assigning lower-level roles like Editor or Contributor where full admin privileges are unnecessary.
Remove unauthorized files
Detecting and removing unauthorized files from your WordPress installation is crucial for maintaining the integrity and security of your website. Malicious or unexpected files can be indicators of a hack or security breach, potentially harming your site or your visitors. Utilizing security plugins like Wordfence or services like Sucuri can significantly simplify this process.
Using Wordfence for file scans
Wordfence is a popular WordPress security plugin that includes a comprehensive file scanning feature designed to detect malicious code, backdoors, and unauthorized file changes.
- Log in to your WordPress dashboard.
- Navigate to Plugins > Add New, and search for Wordfence.
- Click to Install then Activate the plugin.
Once activated, Wordfence will add a new menu item to your WordPress dashboard.
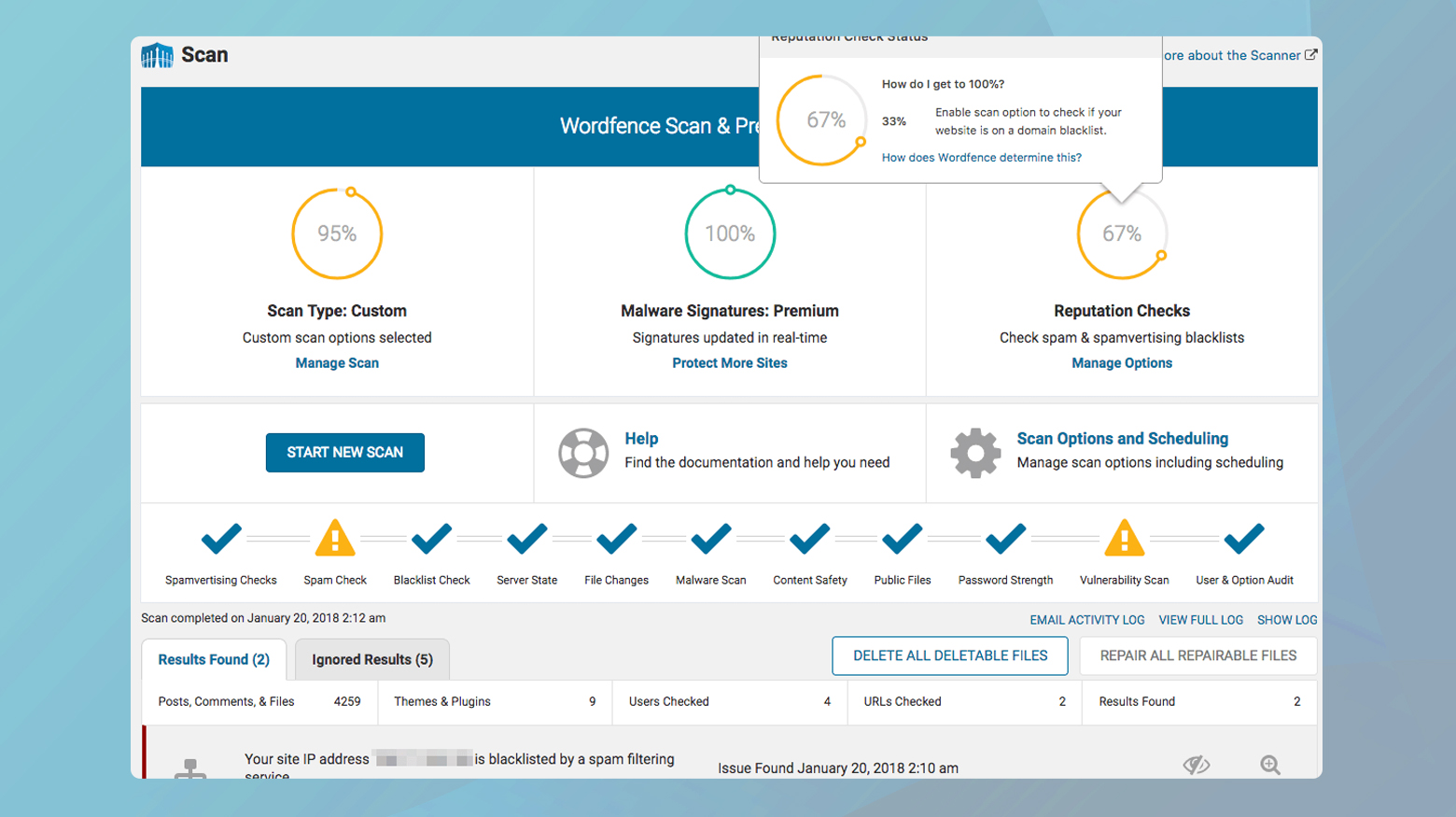
To run a scan:
- Click on Wordfence > Scan.
- Press the Start a Wordfence Scan button to initiate a scan of your site.
After the scan completes, Wordfence will present a list of findings. This includes any files that don’t belong, are out of place, or have been modified in a suspicious manner.
Wordfence allows you to view details of each issue, helping you decide whether to delete, repair, or ignore the flagged files. If you’re unsure about a specific file, research or seek expert advice before taking action.
Using Sucuri for website security
Sucuri offers a range of website security services, including malware scanning and removal. While they have a WordPress plugin, their full suite of services extends beyond what the plugin offers.
Start with Sucuri’s free SiteCheck tool available on their website. Enter your site’s URL to run a remote scan that can identify known malware, blacklisting status, website errors, and outdated software.
For a more thorough cleanup and ongoing protection, consider subscribing to one of Sucuri’s paid plans. These services include website firewall protection, continuous monitoring, and professional malware removal.
Regenerate your sitemap
A compromised sitemap.xml file can significantly impact your website’s visibility and reputation by leading search engines to flag your site as unsafe or compromised. Cleaning and regenerating your sitemap is a crucial step in the recovery process, ensuring that search engines index your site correctly.
Regenerate your sitemap
Many WordPress sites use SEO plugins like Yoast SEO, All in One SEO, or Rank Math to generate and manage their sitemap.xml files. Determine which one your site uses.
Access the settings of your SEO plugin. There should be an option to view, generate, or regenerate your sitemap. Follow the plugin’s instructions to create a new, clean sitemap. This action should automatically remove any malicious links or foreign characters that were injected.
Before proceeding, review the newly generated sitemap to ensure it looks correct and free of any suspicious entries. You can access your sitemap typically by going to yourdomain.com/sitemap.xml.
Submit to Google Search Console
If you haven’t already, adding your site to Google Search Console (GSC) is essential for any site owner. GSC provides valuable insights into your site’s presence in Google search results and allows you to communicate directly with Google regarding your site’s status.
o to Google Search Console and add your site as a property. You’ll need to verify your ownership of the site, which can be done in several ways, including uploading a file to your server or adding a meta tag to your site’s homepage.
Once your site is verified, you can submit your sitemap to Google.
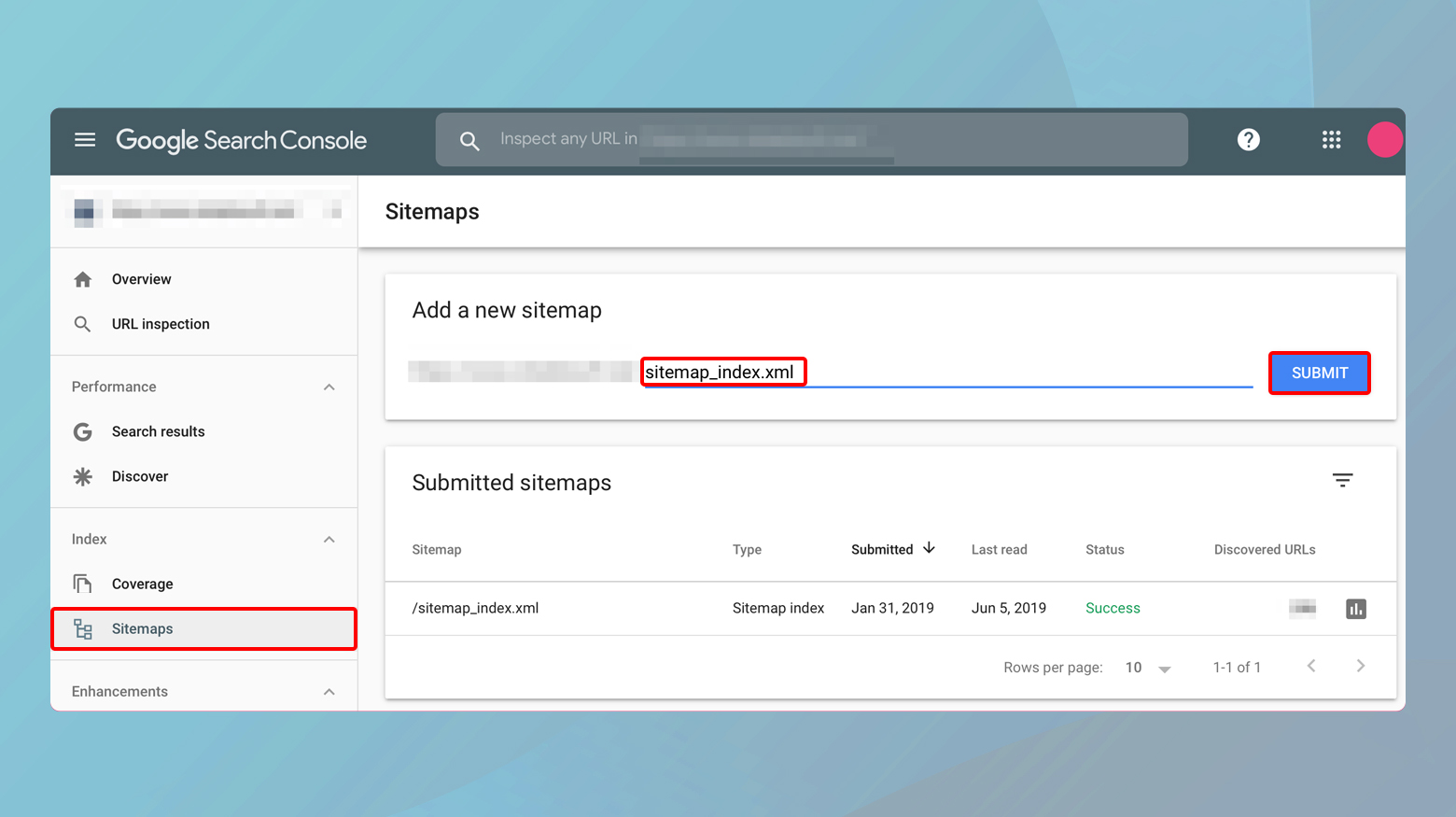
- In the Google Search Console, select your property (website).
- Navigate to Sitemaps under the Index section.
- Enter the URL of your sitemap (e.g., `sitemap.xml`) and click Submit.
After submission, keep an eye on the “Sitemaps” section in GSC. You can check for any errors reported by Google and see how many pages are indexed.
If your site was flagged or penalized due to the hacked sitemap, you would need to request a review from Google.
Cleaning and optimizing your database
If your WordPress database has been hacked, it can result in a range of issues from spam content appearing on your site to unauthorized administrative access. Identifying and cleaning a compromised database is critical for restoring your site’s integrity and performance.
Identifying a compromised database
Security solutions like Wordfence, Sucuri, or iThemes Security can scan your site and identify malicious changes or injections in your database. These tools often provide alerts if they detect compromised elements.
If you’re comfortable with database management, you can manually inspect your WordPress database using tools like phpMyAdmin. Look for unusual or suspicious entries, especially in the wp_options, wp_users, and wp_posts tables. Signs of compromise include spammy content, unexpected admin accounts, and strange links or script injections.
The Ninja Scanner plugin offers a feature to scan your database and file system for malware and suspicious code. It’s a useful tool if you prefer a dedicated solution for scanning beyond what general security plugins provide.
Cleaning and optimizing your database
Before making any changes, ensure you have a complete backup of your WordPress database. This allows you to restore your site if something goes wrong during the cleanup process.
WP-Optimize is a plugin that not only cleans your database by removing stale and unnecessary data but also offers options for optimizing its structure.
- Install and activate WP-Optimize from the WordPress plugin repository.
- Navigate to the WP-Optimize menu in your WordPress dashboard.
- Use the database features to clean out post revisions, transient options, and other data that can accumulate over time. Be cautious with deleting data and ensure you understand what each option does.
If you’ve identified specific malicious entries during your inspection or via a security plugin, you can manually remove these using phpMyAdmin or a similar database management tool. This step requires care and understanding of the WordPress database structure to avoid accidentally deleting important data.
After cleaning your database, change the passwords for your WordPress admin users, your database, and update the security salts in the wp-config.php file. Changing salts will log out all users and require them to log in again, invalidating any unauthorized sessions.
Cleaning a hacked database is a delicate process that can significantly impact your site’s functionality if not done correctly. If you’re not comfortable performing these tasks yourself, consider seeking assistance from a professional WordPress security service. Regular maintenance and monitoring can help prevent future database compromises.
Preventative measures
Preventative measures are crucial in safeguarding your WordPress site against potential threats and minimizing the risk of future hacks. Implementing strong security practices not only protects your site but also preserves your reputation and ensures a safe experience for your users. Here are key strategies to enhance your WordPress site security:
Keep everything updated: Regularly update your WordPress core, plugins, and themes. Updates often include security patches for vulnerabilities.
Use strong passwords and user permissions:Implement strong, unique passwords for your WordPress admin, FTP accounts, database, and hosting control panel. Encourage users to do the same. Limit user permissions according to need. Not every user requires administrative access.
Implement Two-Factor Authentication (2FA): Add an extra layer of security by requiring a second form of identification beyond just a password.
Install a WordPress security plugin: Use security plugins like Wordfence, Sucuri Security, or iThemes Security for regular malware scans, firewall protection, and to monitor suspicious activity.
Use a secure hosting provider: Choose a hosting provider known for its strong security measures and positive reputation. Many offer WordPress-specific hosting plans with enhanced security features.
Backup your site regularly: Maintain regular backups of your WordPress site and database. Use a solution that allows for easy restoration in case your site is compromised.
Enable SSL encryption: Use SSL (Secure Sockets Layer) to secure data transfer between your website and your visitors, protecting sensitive information like login credentials and personal data.
Harden your WordPress site: Follow WordPress hardening best practices, such as disabling file editing, protecting the wp-config.php file, and changing the default database prefix.
Limit login attempts: Restrict the number of login attempts to prevent brute force attacks. Most security plugins provide this feature.
Remove unused themes and plugins: Delete any inactive or unnecessary plugins and themes. Each one potentially adds vulnerabilities to your site.
Use CAPTCHAs for forms: Implement CAPTCHAs on login, registration, and comment forms to reduce spam and automated attacks.
Disable XML-RPC if not needed: XML-RPC can be a target for brute force attacks. Disable it if you don’t use it for mobile app or remote connections.
Closing thoughts
Throughout this blog, we’ve explored various aspects of WordPress security, from identifying and addressing a hack to implementing robust preventative measures to safeguard your site against future threats. By understanding the significance of regular updates, strong password policies, and the use of reputable security plugins and services, you can enhance your site’s defense mechanisms. Remember, security is an ongoing process that requires vigilance, prompt action, and a commitment to best practices. Whether you’re recovering from a hack or looking to fortify your site proactively, the steps outlined in this blog provide a solid foundation for maintaining a secure and trustworthy WordPress site. Stay informed, stay prepared, and keep your WordPress site protected against the ever-evolving landscape of online threats.