The SSH (Secure Shell) protocol is a method widely used for secure remote login from one computer to another. It provides encrypted connections for network services over an unsecured network, like the internet. However, it’s not uncommon to encounter the frustrating SSH Connection Refused error. This error is a signal that your attempt to connect to a server via SSH was not successful. At its core, this error stems from the SSH client’s inability to establish a connection with the SSH server. It’s a bit like trying to make a phone call and constantly getting a busy signal, indicating you can’t get through.
Say goodbye to website errors
Achieve peace of mind with 99.99% uptime on 10Web Managed
WordPress Hosting, powered by Google Cloud.
Defining SSH and it’s usage
SSH offers more capabilities than FTP, which is primarily used for uploading, deleting, and modifying files on a server. SSH, on the other hand, enables a broader spectrum of functions. For example, if you encounter an issue that prevents you from accessing your WordPress website, SSH provides a means to remotely connect and address the problem.
SSH also grants access to a variety of essential tools for developers:
Git: A version control system crucial for tracking code modifications. This is particularly beneficial for development teams collaborating on a single project.
Composer: A tool for managing PHP packages. It assists in integrating various frameworks into your website’s code by sourcing the necessary libraries and dependencies.
WP-CLI: This is the WordPress Command Line Interface. It facilitates diverse tasks like creating new WordPress installations, updating multiple plugins simultaneously, and importing media files.
npm: A package manager for JavaScript. It encompasses both a command-line interface and a registry for JavaScript software.
It is important to recognize that using SSH involves advanced technical skills. For typical WordPress users, it is advisable to seek assistance from developers or hosting providers rather than attempting to tackle issues via SSH independently.
Same issue different message
The SSH Connection Refused error can manifest in various forms, depending on your operating system, SSH client, and network configuration. Some common variations include:
- Connection refused error on attempting SSH login.
- SSH: connect to host port 22: Connection refused on Linux or Unix-based systems.
- Network error: Connection refused in SSH clients like PuTTY.
- The remote system refused the connection on different SSH clients.
- Could not open connection to the host, on port 22: Connect failed in Windows environments.
- Timeout errors that indicate a failure in establishing an SSH connection.
Reasons why this error occurs
Several factors can lead to an SSH Connection Refused error. Understanding these reasons is crucial in troubleshooting.
SSH service not running on the server
The SSH service, managed by the SSH daemon (sshd), must be actively running on the server for a successful connection. If this service isn’t running, your SSH client cannot establish a connection, leading to a refusal. Common reasons for sshd not running include server reboots without automatic service restart, manual service shutdowns, or errors in the server that cause the service to crash or fail to start.
Incorrect SSH port or IP address
SSH connections default to port 22. However, for security reasons, some servers operate SSH on a different port. If you’re attempting to connect to the default port while the server is listening on another, the connection will fail. Similarly, connecting to the wrong IP address leads to a similar dead end. Ensuring that you have the correct IP address and port for your SSH connection is crucial. You can verify the port in the server’s SSH config file (/etc/ssh/sshd_config) under the Port directive.
Incorrect credentials
When attempting to establish an SSH connection, providing the correct credentials is crucial for a successful login. Credentials typically refer to the username and password or, in more secure setups, an SSH key pair. When these credentials are incorrect or mismatched, the SSH server will refuse the connection. This refusal is a security measure to prevent unauthorized access.
Firewall restrictions
Firewalls act as gatekeepers for network traffic. If a firewall on your local machine, within your network, or on the server is configured to block the SSH port (typically port 22), it will prevent an SSH connection. To resolve this, you need to adjust the firewall settings to allow traffic through the SSH port. This involves setting up rules in the firewall configuration to accept connections on port 22 (or your custom SSH port).
Network issues
Network-related problems can vary from simple DNS misconfigurations to more complex issues like server downtime or network outages. An incorrect DNS setting can lead your SSH client to attempt a connection to the wrong server. Tools like ping and traceroute can be helpful in diagnosing such network issues.
SSH key problems
SSH keys are a secure method of authentication but can be a source of connection problems if not managed correctly. Key-based authentication issues can arise from mismatched keys (where the server doesn’t have the correct public key), corrupted key files, or incorrect file permissions on the keys. Ensuring that your public key is correctly listed in the server’s `~/.ssh/authorized_keys` file and that your private key has the appropriate permissions set (usually `600`) are vital steps in resolving these issues.
Server configuration issues
Misconfigurations in the server’s SSH configuration file (`sshd_config`) can lead to a range of issues, including connection refusals. Examples include restricting SSH access to certain IP addresses, using non-standard ports without proper client configuration, or disabling key-based authentication when it’s the only method allowed by the client. Careful examination and editing of `sshd_config`, followed by restarting the SSH service, are necessary to resolve these issues.
MaxStartups exceeded
The MaxStartups parameter in sshd_config defines the maximum number of unauthenticated connections to the SSH server before it starts dropping new requests. This setting helps mitigate certain types of Denial of Service (DoS) attacks. However, on a busy server, legitimate SSH connection attempts might be refused if this threshold is too low. In such cases, increasing the MaxStartups value can help accommodate a higher number of simultaneous connection attempts.
Say goodbye to website errors
Achieve peace of mind with 99.99% uptime on 10Web Managed
WordPress Hosting, powered by Google Cloud.
Steps to fix the SSH connection refused error
To fix the SSH Connection Refused error, we need to approach this issue systematically, addressing each potential cause one by one.
It’s important to note that troubleshooting SSH should be done by people with advanced technical knowledge and skills. Please contact a developer if you are not qualified to troubleshoot this error.
Check if SSH server is running
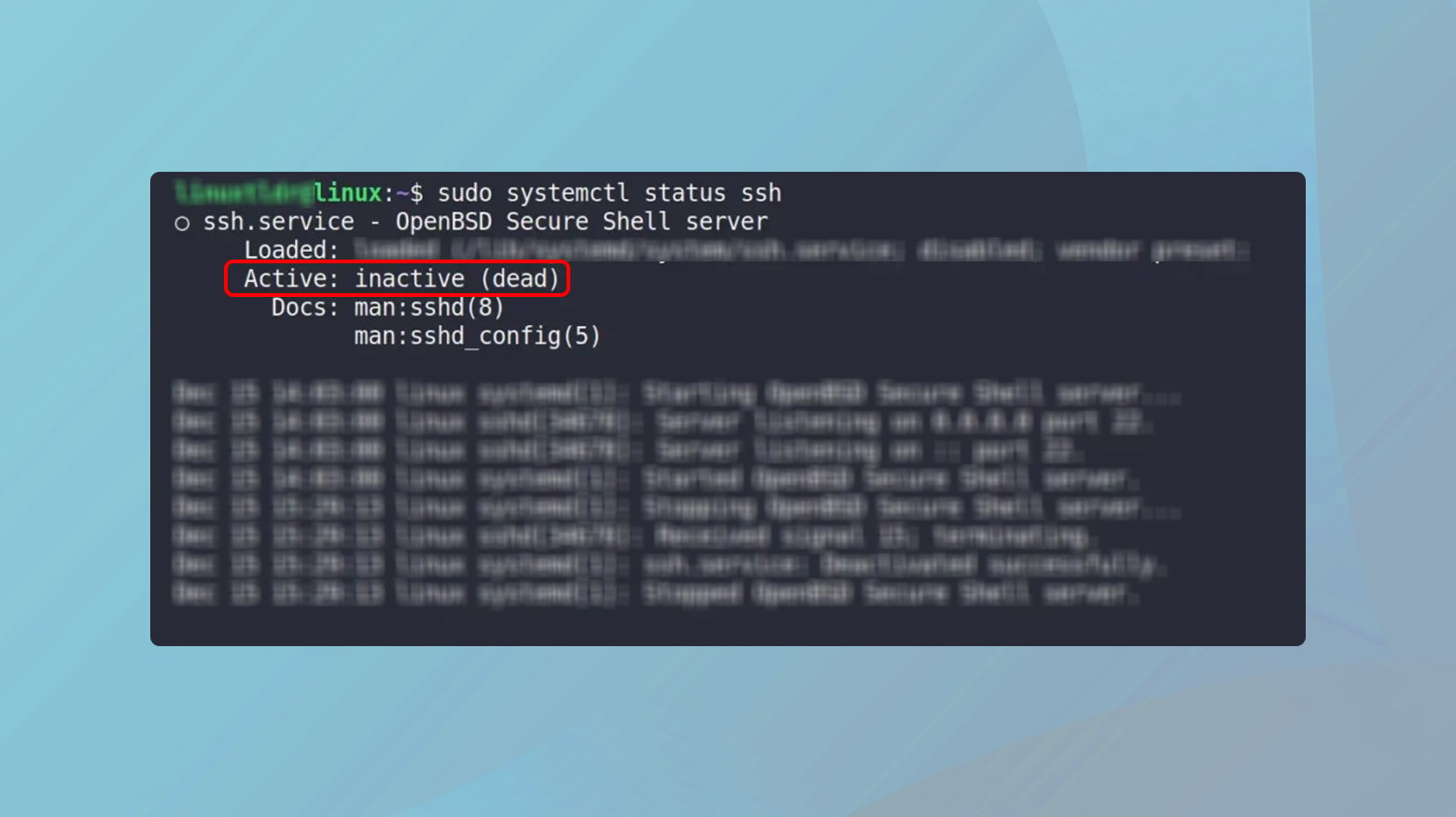
When you initiate an SSH connection, your request is directed to this service. If the SSH service isn’t running, your connection attempt finds no respondent, resulting in a ‘Connection Refused’ error. This is similar to trying to call a business after hours when no one is there to answer. Using sudo systemctl status ssh checks the operational status of the SSH daemon, which manages incoming SSH connections. If the service is inactive or stopped, your connection can’t be established.
To check if SSH is down:
- Open the terminal.
- Type sudo systemctl status ssh and press Enter. This command checks the status of the SSH service.
If the command returns a response of down, dead, inactive, etc., then the SSH server is not running.
Verify server IP address and SSH port
Ensuring that you’re connecting to the correct IP address and port is like verifying the address and door to enter a building. If either is incorrect, you’ll end up at the wrong destination. The port number, usually 22 for SSH, acts like a specific door into the server. Open ports can be a security risk, as they might provide hackers with opportunities to infiltrate your server. Consequently, ports that are not in use are usually closed as a precaution against such attacks.
Should you encounter a Connection refused error, it might be because port 22 (the default SSH port) or another designated SSH port on your server is closed. To check the status of your server’s ports, you can execute the following command:
- sudo lsof -i -n -P | grep LISTEN
This command will display a list of ports in the LISTEN state. You’re specifically looking for port 22 or the custom SSH port assigned to your server in this list. If you don’t find it, reopening the necessary port is essential to establish a connection to your server.
Inspect firewall settings
Open ports are essential for server connectivity but can also be a security vulnerability, leading to firewalls being configured to block these connections. This protective measure, while effective against hackers, can inadvertently cause issues for legitimate users. If you’re trying to SSH into your server and encounter a ‘Connection refused’ error, it’s possible that your firewall settings are the reason.
To investigate this, you should examine your firewall’s rules. You can display these rules on your command-line interface with specific commands for both IPv4 and IPv6 rules:
- For IPv4 rules, use: sudo iptables-save
- For IPv6 rules, use: sudo ip6tables-save
While the results will vary based on your specific setup, there are key elements to look out for to determine if your firewall is indeed blocking SSH connections:
dport 22: This denotes the destination port, which is typically port 22 for SSH connections.
REJECT: If you see this, it indicates that the firewall is refusing connections to the specified destination port.
DROP: Similar to `REJECT`, this means that connections to the relevant port are being actively blocked.
By searching the output of the above commands for dport 22, you can ascertain whether your firewall is blocking your SSH connection. If it is, you will need to adjust your firewall rules to allow SSH requests through, thus resolving the ‘Connection refused’ error.
Ping the SSH server
When you encounter an SSH connection refused error, it often indicates a problem with the network connection between your computer and the SSH server. Diagnosing network issues is crucial because it helps determine whether the problem lies in the network path or in the SSH server itself. Network-related problems could range from simple connectivity issues, like the server being down, to more complex issues like firewall configurations blocking the SSH port.
Pinging the server helps in determining if the server is reachable over the network. If you receive a response, it means the network connection to the server is intact, and the problem might be elsewhere. A failure to receive a response indicates a network connectivity issue.
Windows
- Open the Command Prompt by typing cmd in the search bar and pressing Enter.
- Type ping [server-address] (replace [server-address] with the actual server IP or hostname) and press Enter.
- Observe if the ping command returns a response.
Mac
- Open Terminal from Applications > Utilities.
- Type ping [server-address] and press Enter.
- Check for a response from the server.
Manage SSH keys appropriately
SSH keys play a vital role in establishing a secure and authenticated connection between the client and the server. When facing an SSH connection refused error, it’s essential to verify that the SSH keys are correctly set up. The error might be due to misconfigured, missing, or corrupted SSH keys. The `authorized_keys` file on the server is particularly crucial as it contains the public keys that are allowed to connect. Ensuring this file has the correct public key and is properly configured is a critical step in troubleshooting SSH connection issues.
Verify your SSH key pair
- Check if you have an SSH key pair generated. Typically, this is found in the ~/.ssh directory.
- If you do not have an SSH key pair or if it’s possibly corrupted, generate a new one using the command ssh-keygen.
A missing or corrupted SSH key pair on your local machine can be the root cause of the connection refused error. Generating a new key pair ensures you have a valid private and public key for authentication.
Check the authorized_keys file on the server
- Log into the server using an alternative method like password authentication if key authentication is failing.
- Navigate to the ~/.ssh directory of the user you are trying to log in as.
- Open the authorized_keys file with a text editor.
- Ensure that your public key is listed in this file. If not, add it.
The authorized_keys file contains the public keys that are permitted to access the server. If your public key is not listed or is incorrectly entered, the server will refuse the SSH connection.
Ensure correct permissions for SSH files
- For the ~/.ssh directory, use chmod 700 ~/.ssh.
- For the authorized_keys file, use chmod 600 ~/.ssh/authorized_keys.
Incorrect file permissions can lead to security vulnerabilities and can cause SSH to refuse connections due to policy restrictions. Setting the correct permissions is essential for secure and functional SSH key authentication.
Verify the SSH configurations
- On the server, check the SSH configuration file (usually /etc/ssh/sshd_config).
- Ensure that key authentication is enabled with the line PubkeyAuthentication yes.
- Restart the SSH service if any changes are made (e.g., sudo systemctl restart ssh on most Linux systems).
Misconfigured SSH settings can prevent key authentication. Ensuring the SSH daemon is configured to accept public key authentication is crucial.
Test the SSH Connection
Testing the SSH connection after making these changes verifies whether the issue has been resolved.
- From your local machine, attempt to SSH into the server again using ssh -i [path-to-private-key] [username]@[server-address].
Adjust MaxStartups
The MaxStartups parameter in the SSH daemon configuration (sshd_config) is crucial in controlling the number of simultaneous, unauthenticated connections to the SSH server. When the server is busy or under a heavy load of SSH connection attempts, reaching the limit set by MaxStartups can lead to new connection attempts being refused. Adjusting this parameter can be a solution if you’re experiencing SSH connection refusals due to a high number of concurrent SSH connections, especially in environments with heavy SSH traffic or during peak usage times.
To adjust the MaxStartups parameter:
- Access the server’s sshd_config file, typically located at /etc/ssh/sshd_config.
- Log in to the server using an alternative method if SSH is not available, like direct console access.
- Open the sshd_config file using a text editor.
- Search for the MaxStartups parameter. It might be commented out by default.
- Modify the value or uncomment it and set a new value.
The `MaxStartups` parameter is defined as `MaxStartups start:rate:full`.
- start: The maximum number of unauthenticated connections before rate-limiting starts.
- rate: The percentage chance of dropping a new connection once `start` is reached.
- full: The maximum number of unauthenticated connections before all new connections are dropped.
For example, setting `MaxStartups 30:50:100` means that once 30 unauthenticated connections are reached, there’s a 50% chance that a new connection will be dropped, reaching up to 100% probability when 100 connections are reached.
- After modifying the sshd_config file, save your changes.
- Restart the SSH service to apply the changes. This can be done using a command like sudo systemctl restart ssh on most Linux systems.
Adjusting this parameter helps in managing a high volume of incoming SSH connections, reducing the likelihood of legitimate connections being refused. Attempt to SSH into the server again from your client machine to confirm if the issue has been resolved.
Consult logs for more insight
SSH log files are like detailed journals that record attempts to access the server. These logs can provide specific error messages or clues about why a connection was refused, much like a diagnostic report. By examining these logs, you can gain insights into the exact nature of the problem, guiding your troubleshooting in a more targeted way.
To view the logs:
- Access the SSH log file, typically /var/log/auth.log.
- Look for entries related to your connection attempts.
- Analyze any error messages or unusual entries for clues to resolve the issue.
Conclusion
Resolving an ‘SSH Connection Refused’ error requires a precise approach to diagnose and address various potential causes, ranging from server-side issues like an inactive SSH service or firewall restrictions to client-side concerns such as network connectivity or SSH key mismanagement. By thoroughly following the outlined steps, each obstacle impeding a successful SSH connection can be systematically eliminated. This process, much like a series of handshakes and identity verifications in a trust-establishing encounter, hinges on a deep understanding of SSH connections. Consequently, a meticulous, patient, and detail-oriented approach is key to effectively diagnosing and resolving these errors, securing a stable server connection.
Say goodbye to website errors
Achieve peace of mind with 99.99% uptime on 10Web Managed
WordPress Hosting, powered by Google Cloud.














